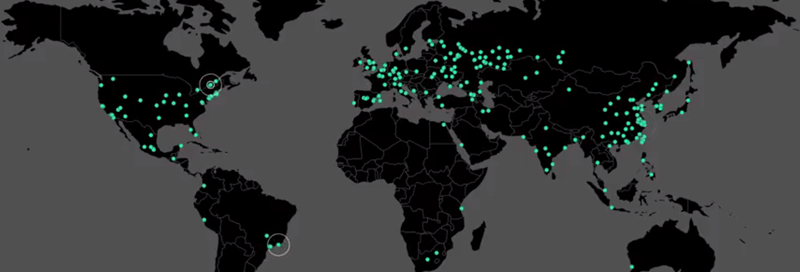
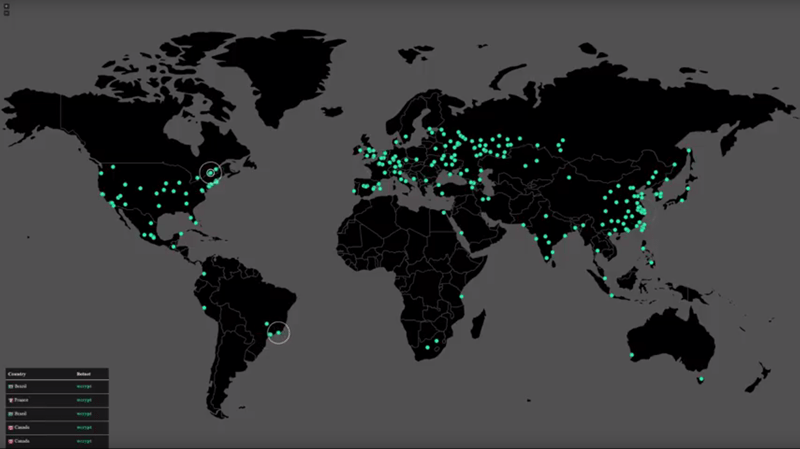
The most extensive ransomware attack in history spread around the globe last week. Utilizing a Microsoft Windows vulnerability and the malicious software meant to exploit it, unidentified hackers used tools first revealed in April after classified information was stolen from the National Security Agency. Within hours, the cyberattack made front-page news around the world, inflicting damage across a wide range of industries, systems, and countries.
By last Tuesday morning, security experts estimated that more than 200,000 computers in 150 countries had been struck by the bold worldwide blackmail attempt. Employees of Britain’s public health service were locked out of computers, systems inside Russia’s highly secure Interior Ministry were afflicted, German train passengers were confronted with ransomware messages at stations across the country, universities in China were attacked, and data was held hostage in Australia, Turkey, India, Italy, Taiwan, the Philippines, Japan, Mexico, and more. Estimates of the economic impact are still being tabulated, but they could easily run into the tens of billions of dollars.
Initial reports suspected that this attack followed standard ransomware procedures: an infected ZIP file is sent via phishing email to an untold number of computer users. When those users inadvertently click on the malicious file, illicit ransomware is quickly installed on the computer. Because the file arrives in an encrypted format, many security systems are not able to immediately detect the problem, allowing the ransomware to quickly spread across any connected drives or networks.
The WannaCry ransomware is different than most cyberattacks
Latest evidence suggests “phishing” emails are unlikely to have caused the WannaCry global cyberattack, however. Security experts have disputed claims that the virus was spread through suspicious emails, speculating that computers were vulnerable to the bug regardless of how vigilant users were. Experts said that unless IT departments patched software and backed up files, they could be hit by the attacks.
What is unusual about this ransomware attempt is its scope, its immediacy, and its multi-pronged nature. The origins of this attack and the people that are to blame have generated a controversy that is causing a media frenzy.
The history of the WannaCry ransomware attack
Reports indicate that months ago the National Security Administration first uncovered a vulnerability in Microsoft’s Windows operating system using a hacking tool that ironically was then released on the Internet by hackers. In March, Microsoft announced that they would release a patch for the problem in their regular monthly security update. But such announcements are often ignored, especially by smaller businesses using outdated and unsupported Microsoft software. Even for larger companies with adequate IT resources, such updates can often take months to fully deploy.
Many security experts speculate that the attack could be executed by hackers that are affiliated with a particular government, marking a critical juncture in the cybersecurity era: it could go down as the first time a digital weapon developed by the US government had been stolen by international cybercriminals and unleashed against doctors, hospitals, patients, businesses, government agencies, and ordinary citizens alike. FedEx, one of the world’s foremost international shippers, was struck at the same time as telecommunications giants like Spain’s Telefónica and Russia’s MegaFon, and many more global behemoths will surely admit to ransomware infections in the days and weeks ahead.
That’s what led to such strong warnings being issued by security experts: Chris Camacho of New York’s Flashpoint said, “When people ask what keeps you up at night, it’s this”; Rohy Belani of email security company PhishMe said, “This is almost like the atom bomb of ransomware.”
How much money is the WannaCry cyberattack costing businesses?
In classic cybercriminal form, the hackers designed the ransomware to increase the amount demanded on a set schedule, threatening to delete hijacked data after a stated amount of time. That raised the crisis-level stakes of the attack and increased the chances that stricken victims would be coerced into paying. As of Tuesday, some experts claimed that less than $1 million had been paid in ransom, although it was not immediately clear how many victims who had paid had actually regained access to their data.
In Great Britain, as the ransomware infections cascaded through scores of hospitals, doctors’ offices, and ambulance companies on Friday, patients were diverted away from emergency rooms, caretakers were left without access to important information, and the government was forced to declare a “major incident,” cautioning residents that local health services could become overwhelmed.
That raised fears about how quickly a small group of unidentified cybercriminals could wreak havoc on global operations. Within 24 hours of the attack, a malware researcher had discovered a “kill switch” to stop the unchecked spread of the malware, but he also issued an ominous warning sure to reverberate in the days and weeks to come: “People need to update their systems ASAP! The crisis isn’t over — all [the hackers] need to do is change some code and start again. Patch your systems now!” And without strong protections in place immediately, some cyber experts expect another wave of infections to cascade in the coming weeks as cyber copycats tweak and repurpose the ransomware code.
How does WannaCry spread?
Security researchers say the ransomware is spread through standard file-sharing technology used by PCs called Microsoft Windows Server Message Block, or “SMB” for short. This makes any organization (like schools, companies, hospitals, and businesses) using networked computers particularly vulnerable. It also appears to be able to spread to other computers outside corporate networks. Researchers have already found variants of the attack, so there is more than just one way it works.
How to know if your computer is infected with WannaCry?
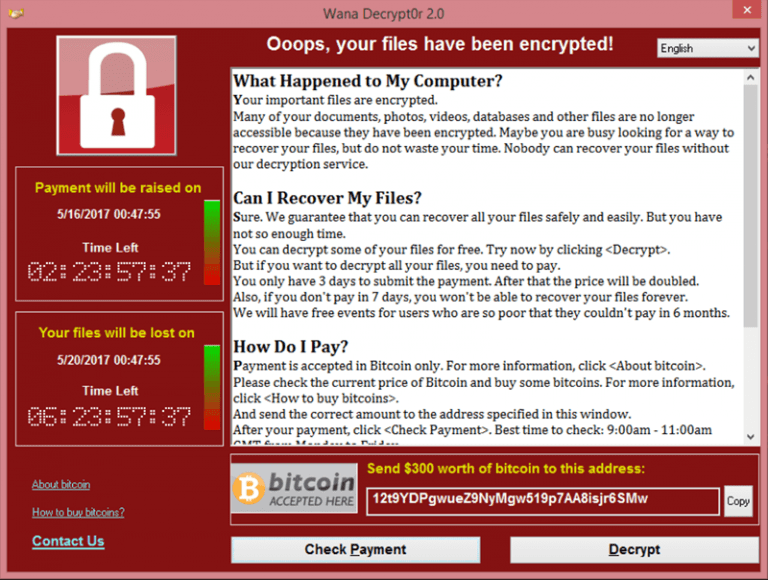
Once a computer is infected with the WannaCry ransomware virus, users are greeted with an “Oops, your files have been encrypted!” message that demands $300 in the form of Bitcoin payment to reinstate access.
If your company computer displays a ransomware message stating your files have been encrypted or another suspicious message, you should do the following:
- Shut down the computer immediately
- Disconnect (unplug it) from all networks
- Contact an IT security expert. Local CMIT Solutions experts are available for assistance.
How to prevent ransomware
Prevention is the best way to avoid becoming a ransomware victim. The virus is primarily targeting older versions of Windows since Microsoft had already released a security patch for Windows 10.
- Updates and Patches
IT providers and security firms are encouraging companies and users to make sure they install the official patch from Microsoft. Make sure your computer is running the latest version of its operating system. If you are a CMIT Solutions client with a Marathon Managed IT Services plan, you do not need to worry about doing this, because we take care of it for you. - Clicks and Downloads
Avoid downloading attachments or clicking on links found in emails from people, companies, or email addresses that you don’t recognize. - Backup and Test
Make sure you regularly back up your data. Many solutions exist on the open market that may lead you to believe you are backing up your entire computer, but if your business relies on technology and the data you have on your computers is critical to your business, then you need to make sure your IT provider is regularly backing up your data to multiple locations in a secure and reliable way. You also want to test your backups, ensure they are functioning properly, and know that you are able to quickly restore the data in the event of a cyberattack or an emergency.
How to protect your business from future cyberattacks
The best way to insulate yourself from such a massive ransomware attack is via a two-pronged security strategy:
- Work with a trusted IT provider to deploy automated security patch and software update delivery, paired with strong enforcement policies and multi-layered network security tools, including anti-virus, anti-malware, and network analysis
- Regularly and remotely back up all data so that, in the case of a ransomware attack, any illicit software can be deleted, computers can be wiped clean, and data can be restored without paying a ransom to an unseen and unpredictable cybercriminal — and without having to lose any critical information.
CMIT Solutions delivers this kind of protection to many of our clients. If you have questions or are unsure about whether your Microsoft Windows operating system received the crucial patch necessary to block this ransomware attack, contact CMIT Solutions immediately.