Last month, CMIT Solutions reported on the threat of the CryptoLocker ransomware virus, which asymmetrically encrypts data with a public and private key and then demands payment for decryption. The original version of the virus required infected users to pay anywhere between $100-$300 in MoneyPak prepaid debit cards within three days of infection or forever lose the ability to recover their data.
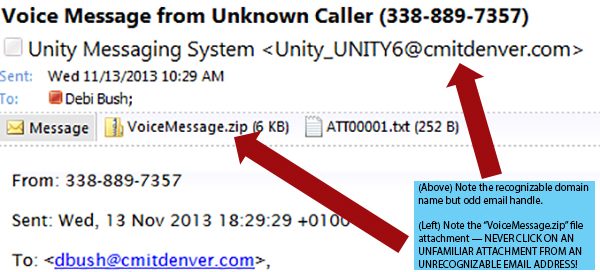
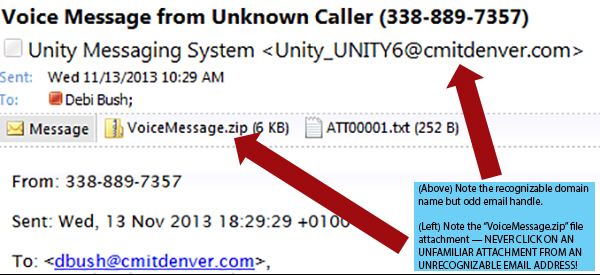
We here at CMIT Solutions are dismayed to tell you that new strains of the CryptoLocker virus are popping up. Previously, most infections took hold after users opened an attachment or clicked a link in a spam email. Now, reports of password-protected ZIP files and voice message alerts from legitimate-sounding addresses have added a new wrinkle to the problem.
Of much greater concern is that certain variations of the CryptoLocker virus are “generously” extending the three-day deadline to pay up and retrieve encrypted data — with a much higher price tag north of $4,000 in unregulated online Bitcoin currency. CNBC reported this week that the hackers behind CryptoLocker have even set up a “customer service” site to handle inquiries about ransom payments and encryption key downloads. As ExtremeTech.com said of the evolution of the scam, “[This] is among the most cynical and cutthroat moves in the history of cybercrime.”
IT experts are still resigned to the fact that little can be done to fight CryptoLocker. Why? The virus employs a mind-boggling level of 2048-bit encryption (the industry standard for secure data storage is 256-bit), making it impractical to decrypt. Previously, even if a business owner pays the ransom (which the United States Computer Emergency Readiness Team doesn't recommend), there was no guarantee that data could be successfully retrieved — hence the new customer service site and extended window to pay. After all, the cyber-criminals behind CryptoLocker are in this to make money.
But paying up past the initial three-day deadline presents its own set of problems. Payment is required in Bitcoin currency, which continues to rise in value relative to the dollar. Also, users are prompted to upload an encrypted file so that an associated private key for decryption can be found. This has two profound impacts: one, contrary to initial claims, CryptoLocker is not deleting infected data after the 72-hour deadline. And two, if an anti-virus program clears CryptoLocker from a machine, a user may lose the ability to access his or her encrypted data, which would prevent the retrieval of the original, decrypted information.
While CryptoLocker continues to evolve, the best steps to avoid infection remain the same:
-
Implement regular, remote backups and a disaster recovery plan. If CryptoLocker encrypts your computer's data, but a backed-up version of that data exists off-site, you can limit the data loss to work performed since that backup. CMIT Guardian can increase your chances of keeping data safe and secure — and help your business survive a catastrophe like CryptoLocker.
-
Never open ANY attachment from ANY unrecognizable sender. Malware attempts are sneaky, and the CryptoLocker virus keeps getting sneakier: emails disguised as social media updates, shipping notifications, voicemail alerts, even fake user handles attached to recognizable (including your own!) domain names. NEVER open an attachment unless you know the person sending it and are expecting a file on the topic mentioned.
-
Hover over ANY link in ANY unfamiliar email before clicking on it. Most email applications allow you to preview a link by moving your cursor over it. Look out for domain names that have no relation to the sender of the email, unfamiliar user handles in front of trusted domain names, or links that appear as an incoherent string of letters and numbers.
-
Ensure that solid firewall, anti-virus, anti-spam, and malware programs are in place. While all it takes for CryptoLocker infection is one person clicking one bad link, these four security features can provide at least a measure of security.
-
Look into whitelisting procedures. Whitelisting can keep employees from running malicious executable files — or provide manual controls over what programs and websites can be opened on company machines.
Worried about keeping your important data safe? Concerned about the threat of one ill-advised click bringing your business to its knees? Call or email CMIT Solutions today to find out how you can successfully fight off ransomware viruses like CryptoLocker.

Leave a comment!
You must be logged in to post a comment.